So, you have a site that many users can access, and you need to be able to define how and users can access the building and what they can do when in the building. What you need is to define the roles users have and a clear overview while still having the ability to quickly define the user’s permissions. What we show in this article is how users permissions work on SPC and how you can configure the system to achieve your goals, we will cover an overview of the structure of users, we will detail user profiles operation and then talk about how this structure works within the wider SPC configuration. We will look at the user rights/alerts and what they do and finally we will look at the tools and services that can support you in your work.
Overview
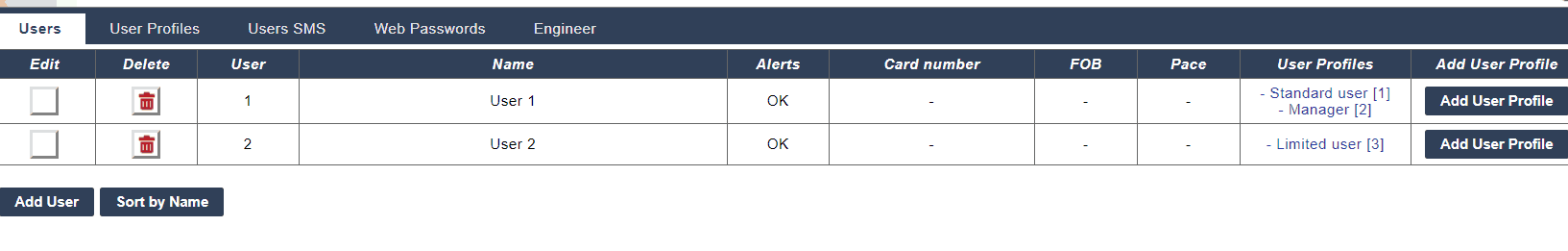
The Vanderbilt SPC system provides support for up to 2,500 users each of which can perform various roles and have different permissions. Each user is given a name to identify the user, you can also define the user’s language this will impact all the local services so that keypads are in the user’s language by default the user will use the systems language but if you want to change it you can.
PIN
Each user on SPC will have a unique pin this will identify the user when they access the system using the PIN, The SPC will also allow the PIN to be ‘0’ this can be used if you want the user to have no intrusion rights, the user may still be given access rights. A key setting with the PIN is the number of digits that your system requires, this is a global setting that is configured in System options and the SPC can support 4,5,6,7 or 8-digit pins. The SPC provides advanced functionality for the management this includes secure pin, forcing pin changes and limiting the pin changes.
Enhancing pin security
PACE
Each user can be assigned a PACE which can be used to access keypads, this can operate in two ways firstly if you assign a pace to a user it will work as an alternative to the PIN, you can also if you wish to enhance security in the system options you will find the setting Pace and Pin, if this is enabled the user will require a PACE and Pin to access a keypad. Using PACE on its own can be very useful for users who may not be comfortable using the keypad to enter pins.
Guard access - Alarm Access
This right will change this user from a standard user to a key holder user, learn more here
SMS
Each user can be assigned an SMS number that can be used to report events or to control the system a full guide on how to configure is available here
FOB
A user can be assigned a wireless FOB that can be used to arm disarm the system or to control outputs on the system. A full guide to the new wireless range available for SPC is available here
Access Control
Each user on SPC can also be given a card, this mean the access permission and intrusion permissions are interlinked and the rights a user has work across both the access and intrusion systems. The are a number of attributes that can also be assigned to a user in order to offer better control of the system, these include extending the time available, escort, Custodian. A full guide on how to configure the system is available here and a full range of hardware is available to support you find out more about readers and door controllers here.
User Profiles
User profiles are the cornerstone of the permissions system within SPC, with them you can set up systems quickly while also being able to define complex relationships. There a few concepts with user profiles and once these are understood the programming will become very simple,
the first is that if any profile gives you permission you have permission to perform the action. A user can have up to 5 profiles each profile can have different rights at a different time but the individual user has the combined rights of all the profiles.
The Second principle is that a user can only see what they are allowed to see, sounds obvious there to more to this than you may first think, the SPC has been designed to support multi-tenant so with this in mind a user can only see another user if they have a) the users right and second that user has the same or fewer rights than that user. What this means is that you cannot see users who are part of another subsystem. When you consider this, you will be able to set up subsystems or even groups with SPC that will only be able to assign rights to add users within their own permissions.
The Third principle is that users are generic profiles are specific, you can program the same user with the same pin on a different pin on a different SPC and it will work, the user profile contains the specific information related to the site. So, the profile will define which areas this profile applies to, this will define which rights can be applied to this area. It will also define the which doors can be accessed by this profile.
let’s take a real-life use case…..
Example 1
A system that has a number of areas, in this system we have a common area and a special area that the disarming of this area will be restricted and only allowed within a certain time. We create a profile that will define the general rights and access we do not include the special area, we then create a new profile that will define the special area and in this profile we can assign a calendar (learn how to configure calendars here), only the users who will be allowed to unset this area will be given this profile.
Rights
The SPC user management system provides several rights to allow to control user’s actions that are allowed on the system. The rights are broken into several sections for simplicity.
Intrusion rights
You can define separately what actions a user can take on an area, so that a user can be allowed to arm/fullset the system but not allowed to unset, this covers all the modes possible for an area. The other intrusion rights define rights that impact the operation of the intrusion system, these include
Force set – this will allow a user to arm the system if there is a zone open or an alert is active, and the user can inhibit. When the user completes the force set they will be informed that there is an issue and the user can force which will inhibit the issue. Any item that is inhibited it will no longer activate an alarm, once the system is unset the inhibit will be removed.
Delay Auto set – This will allow a user to postpone the auto arm of an area, this is dependent on the auto arm configuration for the given area. The user will only be allowed to delay for time and amounts defined by the area
Restore – This will allow the user to restore alerts on the system
Inhibit/isolate – this will allow the user to bypass alerts and disable them on the system, an inhibit will bypass an alert until the next time the area is unset, a isolate will bypass an alert until it is de isolated.
System rights
System rights allow you to define what actions a user can perform, these are more general and work across multiple areas. These include
Web access – this will allow remote access to the SPC system, this includes access via SPC connect
View Log – With these rights users can view the system log
Users – With these rights users can edit and add users with the same or fewer permissions than the user has.
SMS – Users must have the SMS right to configure an SMS for that user
Set date – User can set the date and time
Change Pin – Users can change their own pin only
View video – Users can view the video on their mobile device or on the SPC web page
Chime – User can configure and control the chime function
Engineer/Update – The user can grant access to the engineer to configure the system or/and to update the system
Control rights
These rights determine which elements of the system the user is allowed to control, these include
Outputs – the user can control the mapping gate functionality on SPC via, the app or SPC web page
Door control – the user can control doors locking/ unlocking them
RF output – the user can control the RF output for this area
Test rights
This defines the test functions a user can perform on the system these include
Bell test – this allows the user to test the audible devices buzzer, internal and external bells
Walk test – this allows the user to perform a walk test this can be a key maintenance task to ensure that the system is operational.
Test rights
This defines the test functions a user can perform on the system these include
Bell test – this allows the user to test the audible devices buzzer, internal and external bells
Walk test – this allows the user to perform a walk test this can be a key maintenance task to ensure that the system is operational.
Service level rights
These rights are sub admin rights they are designed to provide a user with permissions to allow them to manage the system, these users should be seen as super users as they can perform operations that can impact the entire system. These include
Set users [master] – this right gives this user rights to access all users and all rights
Set user profiles – this will allow users to create and manage user profiles
Set Calendars – this will allow users to configure calendars from the SPC web page
Level 3 access – users can only inhibit/ isolate according to the standards of the region and the engineer user can inhibit/isolate can perform more actions that a standard user, if this right is assigned then a user can inhibit/isolate with the same rights as an engineer.
Tools
Service level rights
There are a number of tools that can be used to manage users, the main tool that can provide a fast and quick method to program users can be out here
Summary
We hope this overview has shown you the power of the SPC user model and what it can do for your customers. We create this material to support you and if you have any questions please let us know and we can enhance the material available. If you would like to know more about the customer's interface in SPC we have highlighted some below,
SPC Users – Programming setup and options for SPC intrusion system
